At the occasion of the Chaos Communication Congress, a hacker has demonstrated a technique to clone fingerprints from simple digital photos of an individual’s fingers. Politicians and other prominent personalities will now have to keep their hands in their pockets when they speak in public?
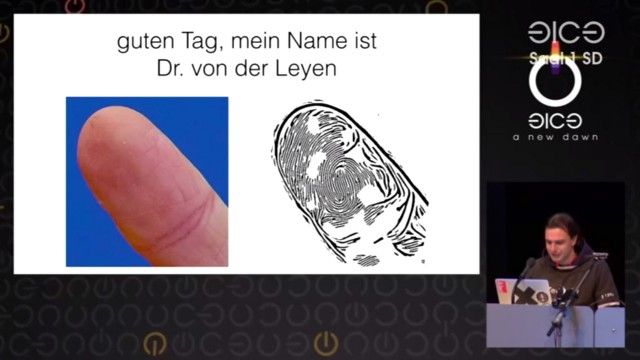
Starbug, a hacker who is a member of the Chaos Computer Club, has shown that it is technically possible to copy fingerprints of a person by using digital pictures of his fingers. During the 31th edition of the Chaos Communication Congress held in Hamburg (Germany), Jan Krissler aka Starbug, illustrated the concept with an example.
He managed to reproduce the fingerprint of the thumb of Ursula von der Leyen, the defense minister of the German government. For this, he used several press photos of the minister showing his fingers from different angles. To clone the fingerprints, Starbug has used the freely available fingerprint software VeriFinger. He then reversed the colors of the resulting image to highlight the features of fingers. This image was then printed to make a mold which can serve as the negative. During his demonstration that is available on YouTube, the hacker has used this false thumb to deceive the finger Touch ID reader of an iPhone.
[youtube]https://www.youtube.com/watch?v=VVxL9ymiyAU[/youtube]
This demonstration using Apple’s smartphone is really striking, this technique can also work with other fingerprint recognition systems that are used to secure access to computers or buildings. “After the conference, politicians are likely to wear gloves when they will speak in public” joked Starbug. If the general public is a priori not directly threatened by this discovery as the implementation is quite complex, it is quite different story for senior executives or researchers who use fingerprint recognition for access to buildings or sensitive data. It is actually quite easy for a hacker or intelligence service to obtain images showing the hands of a politician, contractor or any other person engaged in a sensitive domain.