While public/private key encryption works to allow the distribution of encryption keys across insecure networks and the use of those keys to encrypt transmissions, there is still a problem of knowing if the public key that you have received when you connected to a server is really from the organization it claims to be from.
Perhaps you think you are connecting to www.amazon.com but a rogue computer intercepts your traffic, claiming to be www.amazon.com and giving you a public key to use for encryption. If your web browser trusts the key, it will use the rogue computer’s public key to encrypt your banking information and send it to the rogue computer. Since the rogue computer gave you the public key, it also has the corresponding private key and is able to decrypt and abscond with your banking information.
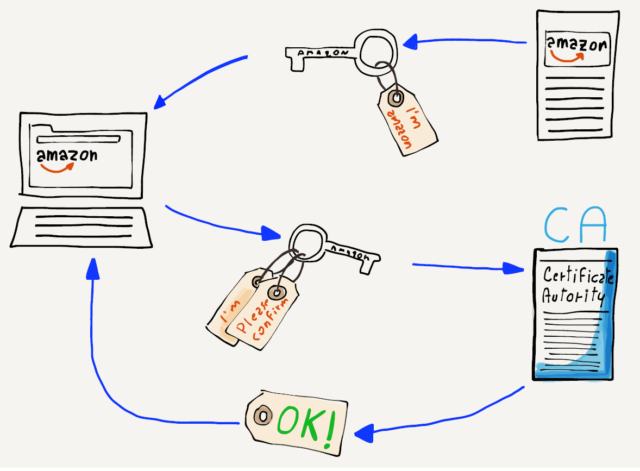
So your computer needs to know who the key is actually coming from. This is achieved by sending you a public key that is digitally signed by a Certificate Authority (CA). When your computer or browser is initially installed, it knows about a number of wellknown certificate authorities. If your browser is given a public key that is signed by one of the well-known certificate authorities, it trusts the key and uses it to encrypt and send your data. If your computer receives a public key that is not signed by one of its trusted certificate authorities, it will warn you before sending your data using the key.
If you see a warning message about an untrusted certificate, you should probably say “no” and figure out why your network traffic is not being routed to the server that you think it is going to before sending any sensitive data.
