When we looked at the Transport layer, we talked about the “window size”, which was the amount of data that the Transport layer on the sending computer will send before pausing to wait for an acknowledgement.
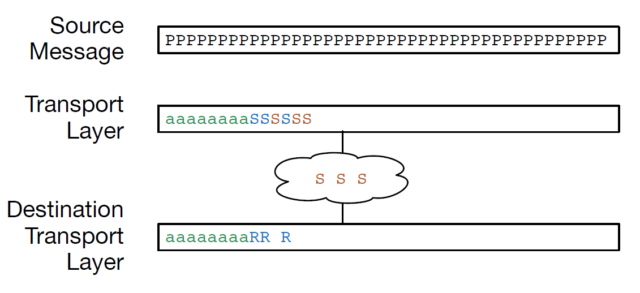
In this figure, we see a message broken into packets, with some of the packets sent and acknowledged. Six packets have been sent but not yet acknowledged and the sending Transport layer has reached the limit of the transmit window, so it is pausing until it receives an acknowledgement from the receiving computer’s Transport layer. The receiving computer has received three packets, one of which is out of order.
When we were looking at this example before from the point of view of the Transport layer, we ignored where the packets to be sent were coming from and where the packets were going to in the receiving computer. Now that we are looking at the Application layer, we can add the two applications that are the source and the destination of the stream of data.
Let’s assume the web browser has made a transport connection to the web server and has started downloading an image file. The web server has opened the image file and is sending the data from the file to its Transport layer as quickly as possible. But the Transport layer must follow the rules of window size, so it can only send a certain amount of data at a time. When the window fills up, the web server is paused until the Transport layer on the destination computer has started to receive and acknowledge packets.
As the Transport layer on the destination computer starts to receive packets, reconstruct the stream of data, and acknowledge packets, it delivers the reconstructed stream of packets to the web browser application display on the user’s screen. Sometimes on a slow connection you can see your browser “paint” pictures as the data is downloaded. On a fast connection the data comes so quickly that the pictures appear instantaneously.
If we redraw our picture of packets in the Transport layer, adding both of the application layers where the packets are in the middle of an image, now it looks like this:
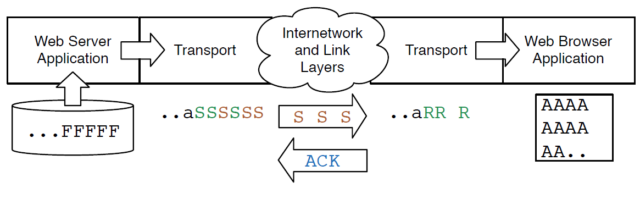
server is reading the image file (‘F’) and sending it as a stream to the web browser as quickly as it can send the data.
The source Transport layer has broken the stream into packets and used IP to send the packets to the destination computer.
The Transport layer has sent six packets (‘S’) and has stopped sending because it has reached its window size and paused the web server. Three of those six packets have made it to the Transport layer on the destination computer (‘R’) and three of the packets are still making their way across the Internet (‘S’).
As the destination Transport layer pieces the stream back together, it both sends an acknowledgement (ACK) and delivers the data to the receiving application (the web browser). The web browser reconstructs the image (‘A’) and displays it to the user as the data is received.
A key thing to notice in this picture is that the transport layers do not keep the packets for the entire file. They only retain packets that are “in transit” and unacknowledged. Once packets are acknowledged and delivered to the destination application, there is no reason for either the source or destination Transport layer to hold on to the packets.
When the acknowledgment flows back from the destination computer to the source computer, the Transport layer on the source computer unpauses the web server application and the web server continues to read data from the file and send it to the source Transport layer for transmission.
This ability to start and stop the sending application to make sure we send data as quickly as possible without sending data so fast that they clog up the Internet is called “flow control”. The applications are not responsible for flow control, they just try to send or receive data as quickly as possible and the two transport layers start and stop the applications as needed based on the speed and reliability of the network.
